What is it?
Today, ninety percent of organizations worldwide now operate in a hybrid or multi-cloud environment. This dramatic shift offers many benefits, such as data privacy, cost savings, and business continuity. But hybrid clouds also come with challenges around providing consistent and comprehensive visibility into a business’s tools without any blind spots. In addition, hybrid clouds add considerable complexity because of their differing orchestration layers and elastic workloads.
Fortunately, Gigamon extends the value of your customers’ cloud, security, and observability tools with real-time network intelligence derived from packets, flows, and application metadata—all of which deliver defense-in-depth and complete performance management across hybrid and multi-cloud IT infrastructures.
Gigamon’s industry-leading visibility tools provide a single consistent access mechanism that is fully integrated with all the major public/private cloud platforms. By using network-derived intelligence and insights, your customers will enjoy a strong value to security posture when used in combination with log-based tools or when this intelligence is used to generate metadata that provides network telemetry in a form that can be consumed directly by security information and event management (SIEM) or visibility tools.
So, let’s learn more about Gigamon’s data-in-motion visibility tools: GigaVUE Cloud Suite, GigaSMART and the Deep Observability Pipeline.
Why should you care?
Achieving visibility into hybrid cloud workloads has always been a challenge. And visibility tools are limited in some way by the telemetry they collect. Many tools rely on logs. But the limitations of logs include data that may be sampled, have insufficient granularity/context, provide minimal network telemetry and context, and that often come with a large amount of “noise” and irrelevant information. In addition, an attacker on a compromised host can disable these data sources and hide their tracks.
Following are examples of additional network visibility tool challenges:
- As network traffic increases, security and performance tools cannot scale as quickly, especially east-west (or lateral) traffic within hybrid clouds.
- Private and public cloud network environments expand and contract dynamically with their respective compute nodes and workloads. The attack surface likewise expands and contracts. Consistent orchestration of packet collection and processing across all these environments is vital for eliminating network blind spots and leveraging a single set of tools across the infrastructure.
- Over ninety percent of lateral traffic is encrypted, creating undetected pathways for for malware delivery and rendering most tools ineffective. Likewise, the large-scale adoption of TLS 1.3 and perfect forward secrecy (PFS) makes most decryption techniques ineffective.
Fortunately, network intelligence derived from packet data collection offers many important and unique security advantages:
- All cyberattacks are conducted and coordinated across the network; therefore, network visibility is a necessary component of your security posture.
- Network packets are an immutable evidence trail of cyberattacks and attackers have no way to know that they are being observed.
- Network detection and response (NDR) is the only method of providing comprehensive real-time cybersecurity capabilities to OT/IoT/SCADA/IoMT environments and it requires packets.
- Detailed L7 metadata based on comprehensive and unsampled packet and session information can provide a previously invisible view of data in motion across an environment to a SIEM and, therefore, to every tool in the SecOps stack.
How does it work?
GigaVUE Cloud Suite
Gigamon’s Precryption technology is a feature of their Universal Cloud Tap (UCT) and also part of their GigaVUE Cloud Suite. Precryption is unique in the industry, as it addresses encrypted east-west traffic between containerized workloads. It works by making a copy of encrypted messages before they reach an encryption library, such as OpenSSL. The encrypted message is then sent to the receiving app on the virtual network with unmodified encryption. This solution works for any encryption method (including TLS 1.3) and avoids the complexity of proxies, key management, and the need to perform expensive decryption.
The Gigamon UCT creates packet headers as needed, encapsulates them in a tunnel, and forwards the traffic to the Deep Observability Pipeline where further optimization and transformation can take place. This is also where any network-derived intelligence (such as port-spoofing detection) can be performed. Ultimately, data is optionally replicated and then delivered to tools, unencrypted.
The following four functions are delivered via the GigaVUE Cloud Suite:
- Gigamon acquires traffic from any on-premises, virtual or public cloud environment using tapping or mirroring tools that are native to the workload. This ensures efficient, high-fidelity traffic capture.
- Gigamon understands this traffic using deep packet inspection. That means, it knows exactly what the traffic is, which tools need to consume it and in what form they need to consume it (packets or metadata).
- Gigamon transforms the traffic and optimizes it for the tools that need it. That could mean something as simple as deduplication/filtering or something more sophisticated like decryption.
- The GigaVUE Fabric Manager provides consistent automation and orchestrated access to all the network traffic on a hybrid infrastructure — eliminating blind spots at any scale. Businesses can then move workloads into production with the required visibility provided automatically. This includes physical, virtual and container traffic across all major hypervisors, hyperscalers and hyperconverged infrastructures.
GigaSMART solutions
Finally, Gigamon analyzes the data and delivers it using the GigaSMART analytic capabilities that are built into the Gigamon Deep Observability Pipeline, as well as more than 200 tools that are also supported. GigaSMART solutions include:
- Traffic intelligence for streamlining traffic
- Application intelligence to filter and extract app metadata
- Subscriber intelligence for advanced 5G networks
- Security intelligence for SSL/TLS decryption
Differentiation in the market
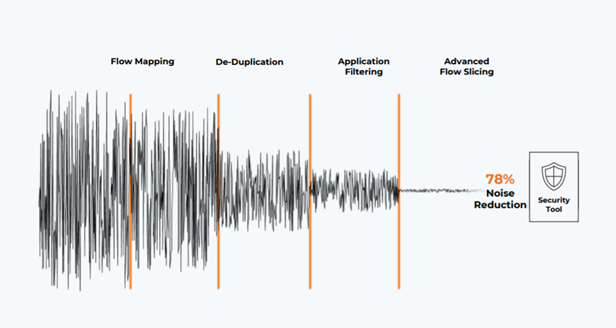
Gigamon has spent 20 years developing its Deep Observability Pipeline that provides unequalled visibility to tools while minimizing tool spend. With Gigamon, your customers can combine or service-chain a range of GigaSMART applications to achieve tool efficiency of 2-3x and reduce the cost of cloud traffic acquisition by up to seventy percent (see graph below). This results in demonstrable savings, especially as companies are stepping up their efforts to control cloud costs.
And with the GigaVUE Fabric Manager orchestration capabilities, the ability to leverage a single tool stack across an enterprise creates improved operational efficiencies.
With Gigamon’s traffic optimization capabilities, businesses can now successively boost efficiency, as well as reduce tool spend.
Arrow and Gigamon: A complete network observability solution set
Arrow’s Gigamon team is made up of experts focused on helping you grow your business and meeting your customer’s network observability needs. In addition, our channel business managers have a deep knowledge of Gigamon’s entire product line and programs. When you partner with Arrow, we will help you integrate Gigamon’s capabilities with SIEMs like Splunk, QRadar, and ArcSight; XDR solutions from Palo Alto Networks, Forescout and Trend Micro; and performance management solutions, such as Riverbed Alluvio.
Arrow’s certified Gigamon engineers have years of experience in selling and supporting the entire Deep Observability Pipeline solution, and they stay on top of all the latest technical developments. Reach out to Arrow today!
More information
- Visit our Gigamon linecard page
- Arrow and Gigamon - Better Together
- 2024 Hybrid Cloud Security Survey
- Acquire Visibility into VMs and Containers
- Application Visibility Across your Cloud Environment
- Detect Port Spoofing Attacks with East-West Network Visibility