Gigamon Precryption redefines hybrid cloud security
What is it?
Gigamon Precryption is plain text visibility of encrypted cloud traffic, but without having to actually decrypt anything. It works for both containers and VMs, in public and private cloud environments, and is unaffected by the cipher used, encryption strength and the use of perfect-forward secrecy (including TLS 1.3).
Why should you care?
All cyber attacks are conducted and coordinated across the network. Network packets are an immutable evidence trail for these attacks and are a crucial part of any cybersecurity defense and detection strategy. Unfortunately, the same encryption methods that allow secure communications across public networks are used by attackers to move undetected within your environment, including public clouds. Modern encryption communications are extremely difficult for security tools to gain visibility into, by design. Virtual networks and workloads further complicate the situation. This creates "blind spots" that help conceal lateral movement, privilege escalation and data exfiltration by bad actors. The only way to regain the advantage over these attackers is to restore the capabilities of network-based security tools by providing them unencrypted views of cloud traffic.
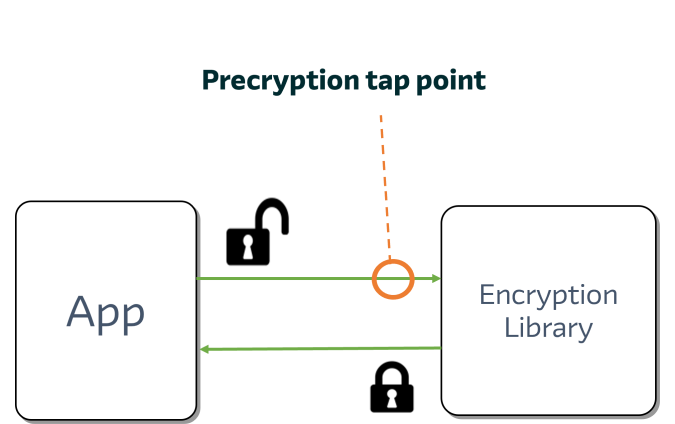
How does it work?
Gigamon Precryption leverages native Linux functionality to listen to the input and output of the encryption libraries such as OpenSSL. It's built on the Gigamon Universal Cloud Tap (UCT), covering most major cloud and virtual platforms. Through special privileges, Precryption can tap the communication between apps and their encryption library and grab the message right before it's encrypted and sent on the network (or alternatively after it's decrypted at its destination).
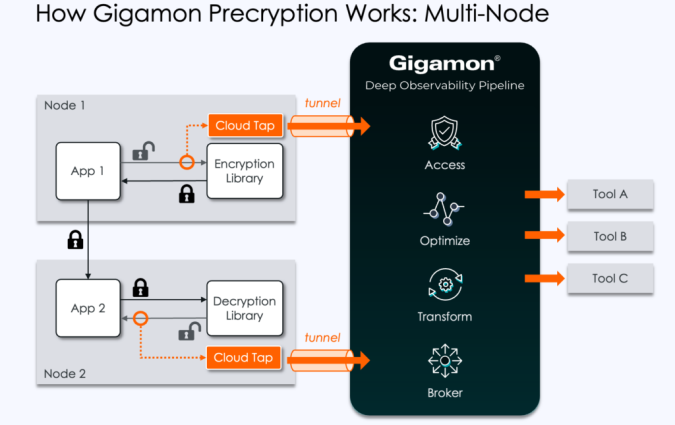
Therefore, Precryption is not actually decrypting, which means there's no need to manage, sniff, or expose keys, and key libraries are unnecessary. It also doesn't "break and inspect" the encrypted communications channel by acting as a proxy.
When the Universal Cloud Tap receives an unencrypted message, it sends it to a physical or virtual instance of a V Series appliance in the Gigamon Deep Observability Pipeline (optionally via an encrypted tunnel). At this point Gigamon further optimizes, transforms, and delivers the data tools as either packets or rich network and application metadata.
How is this different than what already exists?
To better understand what a game-changing technology Gigamon Precryption is, let’s look at the two existing methods for decrypting the latest perfect-forward secrecy protocols.
- An inline proxy is a “man in the middle” technique where it is necessary for the proxy to be in the path of the network traffic between two devices. Besides being computationally expensive (especially inside public clouds), it is extremely impractical for east-west cloud traffic. For containers on the same node, you would have to route the traffic outside the node to the proxy and then back. This severely inhibits the speed and elasticity of containerized workloads.
- The second method requires an agent that runs inside the application workload to “sniff” the unique encryption keys used for each session and then transmit them to a tool. The tool then uses the keys to decrypt the associated network sessions. Besides the many operational headaches associated with agents, and the fact that many workloads cannot run with an agent at all, these solutions are often specific to and only work for a single specific tool.
Gigamon Precryption is a far simpler approach to network visibility inside clouds, and in many ways makes running your workloads there an advantage. By making a copy of traffic just prior to encryption, computationally expensive decryption is avoided entirely. New encryption algorithms are no longer a concern. Headaches associated with agents are avoided, and automatic deployment in Kubernetes is supported for easy scaling. Gigamon’s Universal Cloud Tap with Precryption and Fabric Manager allow you to use a single visibility platform across all major environments (AWS, Azure, GCP, VMWare, Nutanix, Kubernetes, on-prem, etc.). Gigamon’s Application Metadata Intelligence then allows you to enrich the capabilities of your SIEM/SOC with more than 7000 traffic-protocol and application-related metadata attributes.
How to position and sell Gigamon Deep Observability and Precryption
Here are some great conversation starters for partners to discuss hybrid cloud visibility and how to get accurate, unsampled and application-aware network telemetry into tools that consume packets, flows, logs or metadata.
- How do you secure your hybrid or multi-cloud workloads?
- How do you acquire – or plan to acquire – East-West traffic within clouds, VMs and containers? Do you have a single consistent approach? Does your approach meet the needs of both inline and out-of-band tools (both virtual and physical)?
- Have you adopted, or is your organization planning to adopt, TLS 1.3? If so, how are you planning to bring visibility to encrypted communications inside the network perimeter?
- How do you currently detect malicious lateral movement inside public/private clouds when the attacker is using encrypted channels?
- How are you extracting traffic within Azure? (They don’t have packet mirroring capabilities)
- Do you have visibility into unauthorized processes running in the cloud (e.g., crypto-mining)?
- Do you have plans for zero trust and are challenged about how to extend zero trust to cloud-based systems?
- Do you have any on-premises tools that you want to also use to monitor or secure cloud workloads? How will you get cloud traffic to these tools? Are you able to mask sensitive data such as personally identifiable information (PII) to meet compliance requirements?
Arrow's Gigamon experts are here to help
Arrow’s Gigamon team can help you grow your business and meet your customer’s cyber security and network visibility needs. Our channel business managers are experts in the entire Gigamon product line and programs. Our certified Gigamon engineers have years of experience in selling and supporting the entire Deep Observability Pipeline solution and stay on top of all the latest technical developments. Reach out to us today!