Medical providers and regulatory bodies throughout the world are recognizing the need for medical consumables that can be electronically tracked to prevent both unintended reuse and counterfeiting. In this article from Analog Devices, learn about the requirements for implementing a secure, low-cost method of authentication that suits both contact and contactless connections for medical consumables across the whole supply chain.
Many medical treatments now rely on the use of advanced technologies embedded into disposable and consumable items. For the purposes of this application note, disposable, consumable, and single-use all generally refer to any medical items that are intended to be used a limited number of times before being discarded. These items cover a wide range of applications from advanced catheter-based probes used in operations to electro-surgical tools, drug-delivery pens, and pharmaceutical vials. Many of these consumables can only be used once before they are discarded, an approach which is governed by medical and patient safety considerations.
To guarantee patient health, many disposables need to be processed, sterilized, and operated under controlled conditions. With some products, after a single use these conditions cannot be guaranteed. Government agencies around the world have recognized the need to control reuse and prevent counterfeiting to address the immense associated risk to patient safety. Authentication and security in medical device design are fundamental to ensuring that limited-use medical products cannot be reused or used too many times, and that counterfeits can be effectively and efficiently detected and removed from the supply chain.
Many consumables now have electronic capabilities that help improve usability and accuracy. For example, many pulse oximetry sensors contain a small memory device and interface electronics that provide the instrument with calibration data obtained during manufacturing. Other information stored by the sensor, or other type of disposable product, helps to identify it to the instrument with which it is used. This helps to ensure the correct sensors are used, safeguard quality control, and track whether the sensor or tool has been used before and, if so, how many times.
Most attention so far by government agencies has been paid to counterfeit pharmaceuticals. However, one step taken with respect to disposable devices was the introduction by the U.S. Food and Drug Administration (FDA) of Unique Device Identification (UDI). This requirement stops short of what is needed to disrupt the sophisticated counterfeiting activities that are encountered in the supply chains of higher-value devices. Figure 1 shows an example of a UDI label.
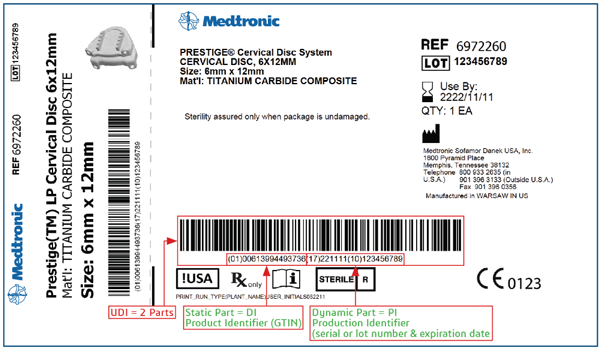
Figure1. Example of a UDI label. (Source: Meditronic)
UDI only requires that the item contain a product identifier in plaintext together with batch and serial numbers and manufacturing and expiration dates. Potentially, these identifiers can be forged or copied and put into use if manufacturers do not take additional steps to control usage.
Electronic protection provides more functionality and control to the manufacturer and can provide additional support for the requirements of UDI and similar legislation by embedding data such as serial numbers in the device itself. However, using the UDI data alone within the electronic protection is not an effective protection because it can be spoofed by a knowledgeable counterfeiter.
An authentication solution can easily be added to a medical disposable with either a contact- or contactless-based electrical interface. For contact applications, the electromechanical connector interface between the disposable and host instrument is normally pin limited, requiring a very efficient solution. Authentication products that operate both power and data over a single dedicated pin address this constraint nicely. For contactless applications, authentication products that operate from a low-cost wireless interface such as RFID/NFC can be utilized. Examples of applications where RFID/NFC is used include consumables that do not require insertion into a host instrument, such as biometric sensor patches, chemical reagent bottles, or containers used for drug/fluid delivery.
At the protocol level, the simplest electronic method for authenticating a device is to set a password that, in principle, is known only to the consumable manufacturer and recognized by any compatible host instrument. When attached, the host requests the password and checks it against its own database. A key drawback is that an attacker can easily eavesdrop on the communication. Once recorded, the same password could be used to authenticate many counterfeit devices.
A better approach is to keep secret identification codes inside the device and use challenge-response protocols to determine whether the product is genuine or not. To maintain better security of such a code, basing the protocol on widely used and carefully analyzed cryptographic authentication mechanisms is an important step. This gives rise to two key types of challenge-response method: one based on symmetric cryptography and another based on asymmetric cryptography.
Symmetric, also known as secret key, cryptography-based authentication revolves around a secret key that is shared by both the host and the consumable, as seen in Figure 2. In a challenge-response protocol, the host sends a random number as its challenge to the device. In return, it expects a digital signature that is generated by a computation based on that random number and the shared secret using a symmetric key algorithm such as a secure hash. The host runs the same computation and, if the response from the consumable is different, it can reject the part. If both computations match, then the device is considered authentic.
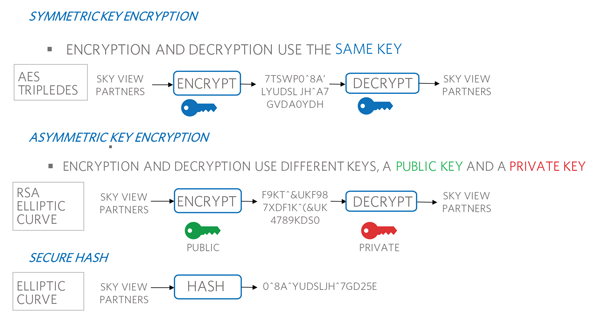
Figure 2. Authentication performed in various types of cryptographic algorithms.
To make sure that a hacker cannot use multiple rounds of challenge and response to reverse-engineer the steps made in the computation, and in doing so retrieve the stored code or key, it is vital that the function have strong mathematical properties and be, in effect, a one-way function. Such a function is easy to compute in the forward direction, but is mathematically infeasible to reverse. The SHA-2 and SHA-3 secure-hash functions are examples of such a one-way function. Both algorithms are collision-resistant—it is infeasible to find more than one input that will produce a given output. A further property is that they possess a high avalanche effect—any change in input, even a single bit, produces a significant change in the result.
Asymmetric cryptography, also known as public key, fundamentally operates with a key pair: a public key and a and private key. The private key that needs to be protected would normally reside in the authentication IC used on the disposable. The host system would use the public key associated with this IC private key. Like the name sounds, the public key can be openly disclosed without risk to the system security implementation. For authentication, this eliminates the requirement for a host system and disposable to establish a shared key like the symmetric case, but at the tradeoff of a significantly more complex math implementation by the host system.
The challenge-response protocol follows the same broad approach as that used for symmetric cryptography. But the host will use the public key from the authenticator to verify the response signature using an asymmetric algorithm such as ECDSA. A successful result obtained using the algorithm proves the device being authenticated has knowledge of the secret, private key. Again, the device proves its authenticity without disclosing the actual key.
The algorithm type, symmetric or asymmetric, that works best for an authentication application depends on a few factors. From a security strength perspective, both are equivalent under typical circumstances. The math for an asymmetric type, such as ECDSA, requires more computing resources than a symmetric type, such as SHA3. However, this can be overcome with a suitable host processor or a dedicated, simple coprocessor. Asymmetric works well if, on the host side, the authentication implementation will be done on a micro and the micro does not have security features to protect sensitive key data. As discussed, the asymmetric public key can be disclosed openly without risk to the system security. Conversely, with the symmetric type, the host side of the solution will need to store a secret that puts the security solution at high risk, if discovered. And, like asymmetric, dedicated coprocessors for symmetric can be used to address the host-side algorithm computation or key storage needs. So, which one should be used? Asymmetric works well when a more rigorous key infrastructure requirement exists. For example, the certificates covered earlier are involved to prove that an authenticator IC public key can be trusted. Symmetric works very well within the deeply embedded boundaries of a host system and the attached disposable or consumable where the public key infrastructure is not required.
With an authentication solution in place, there is the risk that a counterfeiter will be motivated to break the security by attempting to retrieve the cryptographic keys by directly probing and attacking the authentication IC. With this type of attack, determined counterfeiters will use specialized equipment to invasively break into the device package in an attempt to probe internal buses and read or write memory and register contents where a key might be stored. Therefore, countermeasures must be designed into the IC to defeat the threat.
Various methods can be used to address this invasive attack. For example, tamper-detection circuits designed into the IC can actively monitor for probing attempts. If an event is detected, the device will refuse to operate normally and will instead zero out any keys and other sensitive data. Another more recently deployed protection solution is the physically unclonable function (PUF). Fundamentally, PUF is a circuit that is designed to utilize the random variation of electrical characteristics that exists within semiconductor manufacturing to generate a random number. For example, the Maxim PUF-based ChipDNA™ secure authenticators generate keys on the fly based on the precise but random analog characteristics of the IC itself. PUF is perfect for cryptographic key/secret purposes when the value it produces for each IC is random but does not change over all operating conditions and cannot be discovered or reproduced through invasive attack or reverse engineering efforts. Except for the momentary duration of a cryptographic operation, the PUF key value never exists in digital form within the circuitry of the authenticator IC. Further, since the key is derived and produced on demand from physical characteristics of circuit elements, it is never present in the device’s nonvolatile memory. If probed, the sensitive elements that make up a PUF circuit permanently change their electrical characteristics, resulting in a key value that changes and is no longer valid. This effectively renders the authentication IC inoperable, thus a definitive deterrent to any attempt to break the security.
There are numerous ways in which PUF technology can be used for secure functions and authentication. In one use case, ChipDNA based authenticators are installed on the consumable during normal manufacturing. For this example, the PUF output serves as a private key within a public/private key based implementation. Afterwards, during a test or provisioning phase, test equipment sends a command to the hardware and authentication IC to compute a public key based on the private key generated by the PUF core. The actual PUF output value itself is never disclosed or read out from the IC.
Once it has the public key, the medical disposable manufacturer creates a certificate based on both it and their own corporate private key. This certificate is written to protected memory inside the ChipDNA authenticator IC. That certificate will later prove that the public key that the device presents is the same one that was computed at the factory and can therefore be trusted by the medical host instrument—no-one can create a valid certificate without the corporate private key. When used in the field, the consumable signs any message by generating the necessary private key on the fly using the PUF technology. As long as the host instrument holds a public key which corresponds to that device, it can verify that the consumable is authentic.
The secure authenticators in Maxim’s DeepCover® family support a number of features in addition to ChipDNA that are useful for supporting anticounterfeiting strategies and to securely manage medical procedure use. For example, some DeepCover devices include decrement-only counters. When such a counter falls below a set threshold, the host system can refuse to operate until the disposable is replaced with a new unit. Through the use of Maxim’s 1-Wire® interface, both power and serial data can be supplied to the security device, which avoids the need to implement separate power and data connections to the consumable and minimizes the cost of any electromechanical connector. Figure 3 shows some examples of disposable medical tools or sensors using the 1-Wire interface.
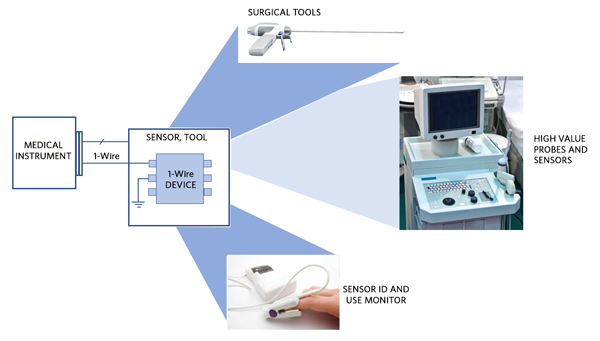
Figure 3. Maxim’s 1-Wire interface in use with medical sensors and equipment.
NFC-enabled authenticators allow use with disposables that cannot implement an electromechanical connector. They also provide a solution for consumables that have no inherent electronic functionality but need to demonstrate to healthcare professionals that they are authentic and validated for use. A further benefit of a number of the DeepCover devices is their ability to survive gamma or E-beam radiation that some medical disposables are subjected to for sterilization. These devices are resistant to up to 75kGy of radiation exposure.
There are numerous ways in which the DeepCover technology can be used. An example is in smart catheters that use technologies such as ultrasound to provide surgeons with a clearer view of the environment inside a patient’s arteries. An ultrasound transducer is embedded in the tip of the device and it reports data back to the host instrument using a serial connection. A DeepCover device operating inside the catheter connector provides the ability to check that it is authentic and unused, and therefore meets all the sterilization and quality requirements of such a critical application.
A DeepCover device embedded in a surgical tool can control authentication using messages sent over a low-cost electrical interface, but also store the calibration data that needs to be added during manufacturing to enable the performance it was designed to deliver.
Nonelectronic disposables with a high inherent value, such as pharmaceutical vials or chemical reagent bottles, can have a small, NFC-enabled DeepCover device embedded or attached to the plastic. A corresponding NFC reader would authenticate the bottle and perform additional protected usage-based writes to the NFC security IC. As disposables and consumables with embedded sensors become more common, the ability to encrypt patient data transmitted to a host instrument will be vital in additional to authentication. This can be supported by embedded DeepCover ICs.
Many other use cases are possible and are enabled by the range of options and functions provided by the DeepCover family of devices, including the optional key/secret personalization service that exists within Maxim's production infrastructure.

