What is RFID?
Today’s radio-frequency identification (RFID) generally takes the form of an RFID tag and a reader. We can trace back the roots of RFID technology to at least the 1940s, when listening devices and transponders identified friendly and opposing aircraft in combat situations. The first patent associated with the abbreviation “RFID,” however, was issued to Charles Walton in 1983. Since then, we have seen these tags form the basis of many different devices, such as:
-Theft-deterrent devices, which use tags attached to clothing and other items
-Access control devices via cards or key fobs
-Inventory management systems to track item locations
NFC, or near-field communication, is a modern subset of RFID. You’ll often see NFC at work in smartphones for identification and payment capabilities. In NFC format, devices can both send and receive messages, making them more capable (at short ranges) than RFID at large.
Examples of RFID
RFID tags take two main forms, passive and active tags.
Active RFID tags: These tags contain a power source on the tag itself and transmit a signal to a passive reader. This setup allows for transmission ranges that can exceed 100 meters depending on the implementation, making them much more powerful than tags in most access card readers.
Another class of tag, the battery-assisted passive (BAP), contains a power source that allows it to send out a signal when an RFID reader is present. Several different frequency ranges are used to establish RFID communications, including the 120-150 kHz range for animal identification, 13.56 MHz for smart card usage, and other frequency bands up to the GHz range.
NFC tags operate in the 13.56 Mhz range and can transmit data such as credit card account numbers, ID codes, and other information. You may also see NFC functionality incorporated into smartphones, which can act as both the transmitter or receiver. With NFC tags, phones with Apple Pay or similar programs can emulate credit cards as well as offer “tap to transfer” services. This type of data transfer service establishes a connection between two phones, then uses Bluetooth or Wi-Fi to transmit the data.
Passive RFID tags: These tags receive power from an active transmitter then send a signal back using a small portion of this energy. Due to their passive design, the power from the reader must be several orders of magnitude higher than the signal the RFID tag transmits, and the transmission range is normally limited to a few centimeters. Passive tags are commonly used in access cards or to track goods, making them the setup that comes to mind when most people hear the term RFID. You can even implant passive tags into or attach them to animals to help return lost pets or manage livestock.
Arduino RFID Reader Setup
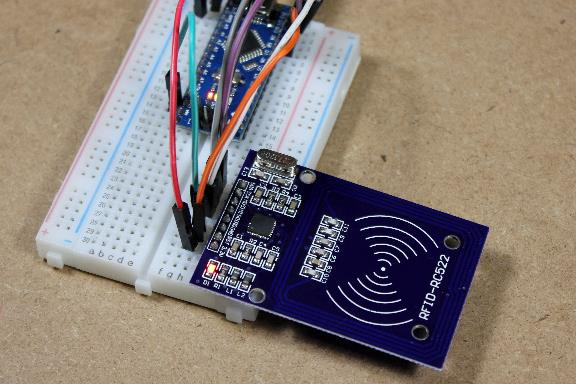
Caption: Arduino RFID-RC522 setup
If you’d like to dig deeper and experiment with RFID, you’ll only need a few supplies:
-RFID-RC522 sensor module
-The corresponding card or key fob
These devices are set up to read and write in the 13.56 MHz range, and there is a handy Arduino library available to get things started called “MFRC522.”
Once you collect these materials, follow these steps:
1. Search for and install the library in the Arduino IDE.
2. Open the “DumpInfo” example sketch. This sketch notes the typical wiring layout for several types of Arduino boards in the comments, though you’ll also need to supply 3.3 V and ground.
3. Load the sketch into your Arduino, then open the serial port to 9600 baud and place your card or tag on top of the reader.
If everything is in order, the device will produce a series of 16 hexadecimal numbers, followed by three sets of 16 hexadecimal numbers that all read 0, then repeat the sequence over and over. This eventually ends, and the last line will be different than the others. This final line signifies the card’s unique identifier (UID) with the first four bits in the last series— block 0. You can also find the UID listed at the beginning of this serial output, matching this block 0 info.

Caption: Beginning of tag data, note UID
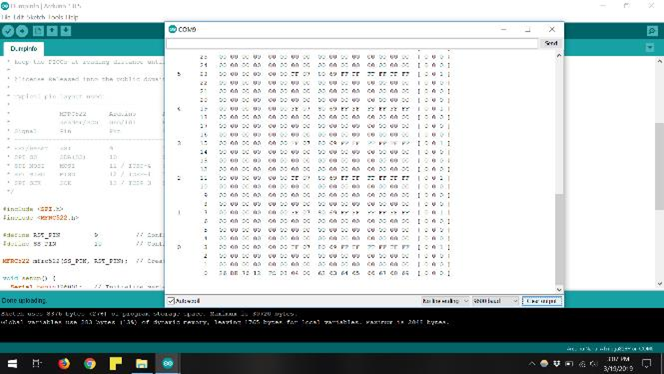
Caption: End of same tag data, note sector 0, block 0 data matching UID
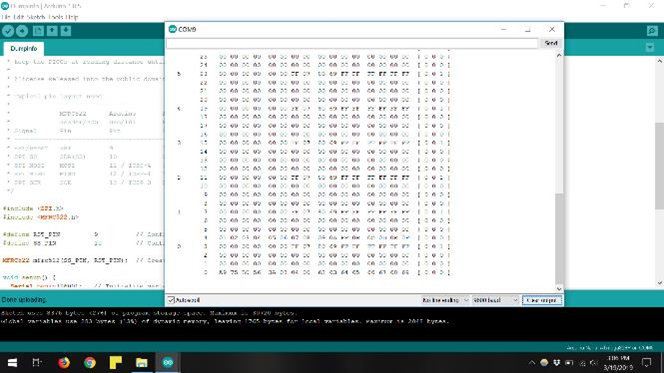
Caption: End of second tag data, note change in sector 1, block 4 data written to card, and different UID in sector 0, block 0
Card readers can use the UID last piece to tell whether someone is, for instance, authorized to enter a particular area. For security purposes, this data is permanent and cannot usually be changed. Writable cards, however, are available, and the library also includes a “ChangeUID” sketch if you’d like to experiment with swapping out the UID. Even if you can rewrite the data, you may end up with a card that won’t work with commercial readers. It seems that reader manufacturers may have implemented countermeasures against this kind of potentially security-compromising activity.
You can’t always change the UID, but you should be able to swap around other data on these cards with a sketch called “ReadAndWrite.” This sketch writes data to the card and then reads it back. The reader will decide how to use this kind of data, but it’s intriguing to have it available. Perhaps you could use it to pass secret messages or act as an input method that actually works as a source of data, without just pointing to a location on a database elsewhere.


